Learn About Secure Boot And How It Improves PC Security
With the growing threat of infectious low-level malware which can get into the boot process to load in malicious programs or prevent an operating system from starting, Intel developed EFI in the 1990s to secure the boot process.
More recently, EFI was superseded by the improved UEFI which continues to see new versions. The most recent iteration added cryptology, network authorization and a few other nice extras.
What Is Secure Boot?
Secure boot is the Microsoft version of the UEFI standard which comes with Windows 8, Windows 8.1, Windows Server 2012, Windows Server 2012 R2, Windows RT and Windows RT 8.1.
For desktops and laptops with Windows 8 or 8.1 installed, to bear the Windows 8/8.1 holographic logo sticker on the computer, the secure boot is required by Microsoft to be enabled.
How Does Secure Boot Work?
With the BIOS that is present in computers, this starts when the PC is booted up and then the Windows boot loader, a Linux boot loader or some other bootable system is started.
Unfortunately, it's possible for malware to change the boot loader entirely in order to load malicious code instead of the operating system installed on that computer. A rootkit can get into the boot system and deliver real pain.
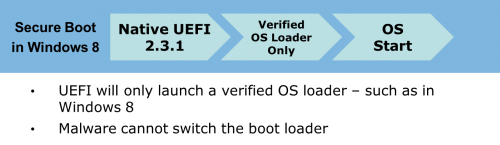
Secure boot requires that all operating systems and other software attempting to load at boot-up will need a verified certificate from the manufacturer. In the case of a Microsoft operating system, the OS will need to be signed by Microsoft Corporation.
Only operating systems that are digitally signed correctly will be allowed to boot, which prevents malware rootkits and other malicious intrusions at the boot level.
Improved Security
Signature databases are checked when a PC is started against the known platform key. If the firmware is not trusted because the key is incorrect then the UEFI firmware will need to recover via the OEM process supplied by the computer manufacturer.
The Windows Boot Manager can be backed up so that in the event of corruption, Windows can recover from backup in order to get Windows started again. The Windows Recovery Environment can also be utilized to resolve driver or kernel issues preventing the Windows Boot Manager from succeeding in booting the installed Windows operating system.
Signing Services
Microsoft is charging operating system manufacturers and software developers like anti-virus companies a $99 fee to be able to digitally sign their operating systems using a Microsoft certificate.
It is also possible to be supplied with a digital certificate by a software developer or to create and sign your own certificate too.
Supported Processors
Versions of UEFI exist that support Itanium, x86 32-bit, x86-64 64-bit and ARM processors.
ARM processors are used mostly in mobile devices like smartphones and laptops presently. 64-bit support for ARM processors was only at proof of concept phase less than a year ago, so clearly secure boot in the mobile computing world is a work in progress.
Support for the other processors above is far more mature.
Turning Off Secure Boot
Secure boot can usually be disabled at the BIOS level. This would invalidate the logo-certified Windows status and technically the logo would need to be removed from the PC to reflect that.
Also see: Microsoft Secure Boot overview.