The Easy Way to Check your System Against Spectre and Meltdown CPU Bugs (and How to Protect it Against these Vulnerabilities)
As you probably read about it already, from January 3rd onwards, two major hardware security flaws have been discovered in modern computer processors. These bugs are named Spectre and Meltdown. You can read about both vulnerabilities at https://meltdownattack.com or https://spectreattack.com - it's the same info on both sites. If you're looking for a non-technical explanation of the bugs, here's one featuring Men in Black and aliens - yep, that just happened.
Should I be worried? What can happen to my system?
Do worry, but don't panic. If you're using a modern system, then that system is probably vulnerable to these CPU bugs.
"These hardware vulnerabilities allow programs to steal data which is currently processed on the computer. While programs are typically not permitted to read data from other programs, a malicious program can exploit Meltdown and Spectre to get hold of secrets stored in the memory of other running programs. This might include your passwords stored in a password manager or browser, your personal photos, emails, instant messages and even business-critical documents." - Source
What processors and systems are affected?
Meltdown is affecting every Intel processor since 1995, except Intel Itanium and Intel Atom before 2013. At the moment, it is unclear whether AMD processors are also affected by Meltdown. According to ARM, some of their processors are also affected. The vulnerable systems are Desktops, Laptops, and Cloud computers.
Spectre is affecting Intel, AMD, ARM processors on all modern systems: Desktops, Laptops, Cloud Servers, as well as Smartphones.
What should I do about this?
Did we mention "Don't Panic" yet? Not a single attack using Spectre or Meltdown has been reported so far. Besides that, while Spectre is harder to fix, it is also way harder to exploit and turned into an attack.
So what are the steps you can take right now, in order to protect your systems?
1. Check if your system is affected by Spectre and Meltdown.
1.1 Windows users (skip to Linux checker if you're not using Windows)
Microsoft put together a PowerShell script that you can use to verify if your Windows system is affected by these bugs. The script with all the info needed to run it can be found here, but it's far from being easy to use by non-tech savvy users. The script can run on Windows Windows 7 SP1, Windows 8.1, and Windows 10.
Luckly, Ashampoo's tool Spectre Meltdown CPU Checker comes in handy here as it is based on that script, but comes with a simple graphical interface that any user can easily understand. Here's the step-by-step how-to on using this tool:
a) Download Ashampoo Spectre Meltdown CPU Checker.
b) Double-click the SpectreMeltdownCheck.exe file - it's portable, no installation required. Click "Yes" for an UAC prompt.
c) Click the "Start security check" button and wait for the program to scan.
If you're having problems here, you should check if you have Windows Management Framework 5.1. If not, get it from: https://www.microsoft.com/en-us/download/details.aspx?id=54616 (KB3191566). It includes updates to Windows PowerShell as well, which is needed to run this app.
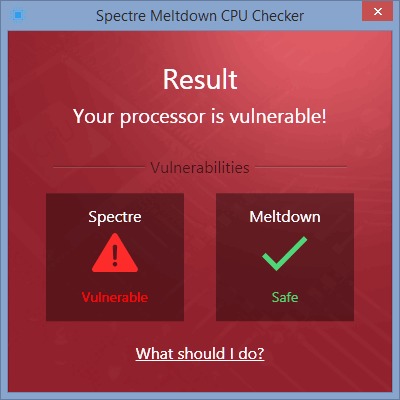
The app will next check for Meltdown and Spectre vulnerabilities and display the results as shown below. Your results may vary.
d) If your system is vulnerable, the "What should I do?" link highlights the same steps that we'll cover below.
Note: Users report a few bugs for Ashampoo Spectre Meltdown CPU Checker and while the developers are currently investigating these issues, the app might not work for everyone just yet. During our tests, it worked well on our Windows 8.1 machine.
An alternative tool to check for Meltdown and Spectre bugs on Windows is InSpectre, by GRC. The app works similar to Ashampoo's Spectre Meltdown CPU Checker, does not require installation, and it shows the required steps to obtain protection against these security flaws. It can also disable protection for both Meltdown and Spectre (launch with administrator privileges in order to do that), useful if you want to compare performance with and without the patches applied.
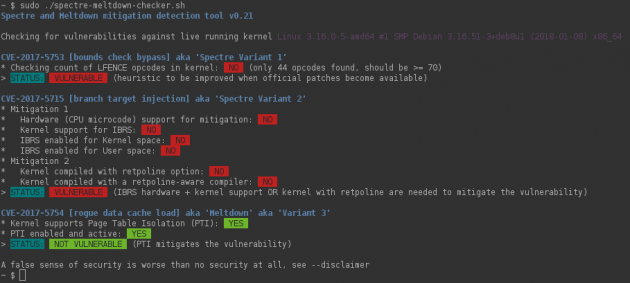
The easiest way to check if your Linux distro is affected by Meltdown or Spectre is with Stéphane Lesimple's tool, Spectre & Meltdown vulnerability/mitigation checker for Linux, which you can download here from GitHub.
Without options, it'll inspect your currently running kernel. You can also specify a kernel image on the command line, if you'd like to inspect a kernel you're not running.
The script will do its best to detect mitigations, including backported non-vanilla patches, regardless of the advertised kernel version number.
This is an example of the script in action; your results may vary
2. Check for OS updates.
Linux distros have all begun to offer kernel updates to fix these vulnerabilities and will continue to do so in the near future. If your Linux distro is not yet offering a security fix for Spectre and Meltdown, then you should probably think about using another Linux distro.
Check Windows for updates and update accordingly. If you previously disabled your Windows updates, now it's a good time to re-enable them.
Apple also released patches for both Meltdown and Spectre. Initially available to macOS High Sierra only, Apple decided to patch macOS Sierra 10.12.6 and Mac OS X El Capitan 10.11.6 as well.
3. Check for UEFI/BIOS updates.
Motherboard manufacturers are already updating their BIOS firmware, although it is unclear if all older models will receive a patch.
Intel, for example, stated that it will release fixes for 90% of all the CPUs released in the last 5 years. AMD said that out of the 3 variants of Spectre, AMD microprocessors are vulnerable to the first two of them only and that they are releasing microcode updates for system vendors to integrate within BIOS/UEFI firmware updates, as well as working closely with OS providers to develop the required patches.
After the microcode updates are released though, each PC manufacturer still needs to embed those processor microcode updates into a firmware, so older models might get skipped in the process.
The best way to go about updating your BIOS/UEFI is by going to your motherboard's manufacturer's site and check the Drivers section for updates to BIOS/UEFI for your specific system/motherboard model.
if you have a Dell PC, like me for example, you can check Dell’s support page for your specific model. Same goes for a Lenovo or Asus PC - check Lenovo or Asus's websites for updated BIOS firmware. If you have a custom built PC, you should check your motherboard manufacturer’s website for an updated firmware.
The actual BIOS/UEFI firmware update process is different from manufacturer to manufacturer so the best way to handle it is to download the updated firmware file and look for a Readme file within it, which should cover all update steps, then go from there.
4. Update your browser and other apps.
All major browsers will release updates which will protect against these vulnerabilities. Chrome will offer these initial fixes in Chrome 64, scheduled to be released on (or around) January 23, 2018 (until then, Google recommends enabling site isolation by entering "chrome://flags/#enable-site-per-process" into your browser's address bar and click "Enable", then restart Chrome), while Firefox already released a fix starting with Firefox 57.0.4, mirrored on our site as well.
If you are using Microsoft Edge or Internet Explorer, the patch is already included in the Windows Update.
While you're at it, make sure all your apps are up to date, since these vulnerabilities can be exploited in apps that interpret untrusted code (in the way web browsers interpret JavaScript code, for example).
5. Video card drivers updates.
While the graphic cards are not hit by these vulnerabilities, Nvidia did start to update its drivers in order to help mitigate the CPU security issue. So, you can update your GPU drivers as well.
We believe our GPU hardware is immune to the reported security issue. As for our driver software, we are providing updates to help mitigate the CPU security issue. - Nvidia
In a general press Q&A, Nvidia CEO Jensen Huang said:
Our GPUs are immune, they’re not affected by these security issues. (...) What we did is we released driver updates to patch the CPU security vulnerability. We are patching the CPU vulnerability the same way that Amazon, the same way that SAP, the same way that Microsoft, etc are patching, because we have software as well. - Jensen Huang, Nvidia CEO
As for AMD, they also made it clear that their GPU line is not affected in any way by Spectre or Meltdown:
There have also been questions about GPU architectures. AMD Radeon GPU architectures do not use speculative execution and thus are not susceptible to these threats. - Mark Papermaster, Senior VP and CTO
6. Be careful with emails and websites
A common way for attackers to get you to execute malicious code is to send that code via email or embed it into websites, so be extra careful when you open emails attachments or when visiting websites.
What next?
The patches will keep on improving when more information is known about the Spectre and Meltdown vulnerabilities, so stay informed and keep your system, applications, and drivers up-to-date.