Is My Mobile Phone Being Monitored? Part 2/2: Necessary Actions To Take
This is the second part of the "Is My Mobile Phone Being Monitored?" series. In the first part you learned how to tell which indications imply a possible phone monitoring, while in this part, you can read what you have to do if you want to defend yourself from these activities.
- Necessary actions to take
- Interference of electronic devices
- Detection of malicious applications
- Disabling Bluetooth
- Limiting internet data usage
- Changing your accounts’ passwords
- Preventing installation of apps from unknown sources
- Performing an anti-malware scan
- Checking for root or jailbreak
- Encrypting the device
- Factory settings
- Request assistance from your carrier and authorities
- Is it possible that your phone is being monitored?
Necessary actions to take
If the signs mentioned in the first part of the article are present in your device, then it is deemed necessary to take actions which shall help get rid of any monitoring activities.
Of course, if the monitoring that takes place has nothing to do with independent malicious applications, but with professional signal interception equipment normally used by government agencies, then it’s quite difficult to block the invasion.

Interference of electronic devices
In this case we can limit the monitoring activities in your phone. What you should do, is stand near electronic devices such as TVs, during phone calls.
The less powerful TV signal may cause some interference, making it difficult to monitor the phone call. However, the problem will still remain and not be eliminated.
Since you’re the target of such tracking services, the only effective solution is the device’s permanent shutdown, and the removal of its battery and SIM card. Then you can proceed into the destruction of the device too, if you have no further need for it, and if you do not consider resorting to the competent authorities.
Detection of malicious applications
Initially, what you need to do is take a look at the device’s statistics regarding battery use. You can find them within the device settings.
From there you can see all known apps that make use of the battery. However, if you find an app that you are not aware of or don’t use often, this may be the spy that monitors your device.
The action in this case is obvious: remove this particular app immediately and without any hesitation.
Typically, malicious device tracking apps are found in devices due to hasty installations. However, a person you trust or know well could also be the one who might have infected the device.
Disabling Bluetooth
As you saw at the beginning of the article, Bluetooth can help those who wish to track your mobile device. Therefore, it is important to use it only when needed, and configure it to not to reveal revealing your device.
The risk of infection via Bluetooth is absent for iOS devices, since such data exchange is not allowed.
However, this does not apply for jailbroken iOS devices, where the Bluetooth feature is unlocked and works like on Android.
Limiting internet data usage
You should not allow any application to enable internet data without your consent, in order to prevent any background malicious activity.
In any case, it is necessary to take control of your internet data regardless of whether you have been infected or not. You can do that by visiting the Data usage section found in the device’s settings, and deleting any app that uses a lot of data without any particular reason.
Changing your accounts’ passwords
If you are suspecting that your device being monitored, then it is more than urgent to change your passwords on every account that you have, with no exceptions.
If you have an iOS device, the first thing you should do is change your iCloud passwords and replace them with stronger ones.
The same should be done in Google’s respective accounts too. Moreover, you have to change all passwords required during device boot procedure.
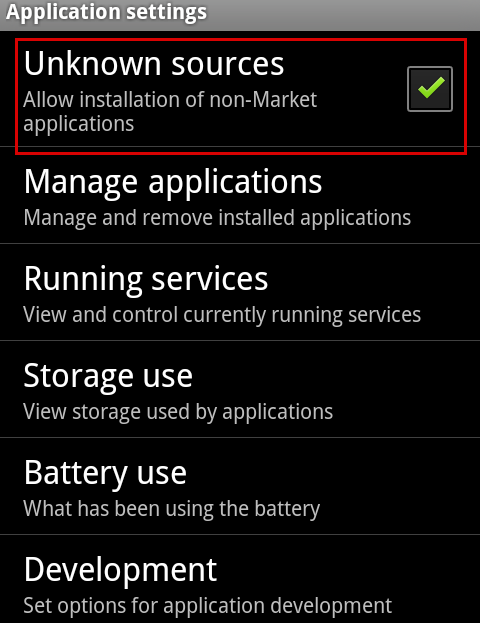
Preventing installation of apps from unknown sources
If you have an Android smartphone, the risk of it becoming infected with a malicious app that will invade your personal life can be reduced if you do not allow installation of apps from places other than the Play Store.
In case the app is not on Play Store, or was found elsewhere for free, you must be absolutely sure that it is trustworthy before downloading it.
Additionally, Android users must check daily for any apps that might have been unintentionally given administrator rights. If you find that apps which you do not trust have been given administrator rights, simply restrict their access again, or delete them if you they are not needed.
Performing an anti-malware scan
Once you notice signs which make you suspect that the device is being tracked by an application, a daily anti-malware scan is necessary.
One of the most appropriate solutions for Android devices is Malwarebytes Anti-Malware, a software mainly known for its effectiveness in cleaning PCs from all kinds of malware.
However, if your device is rooted, the malicious app can successfully hide from the anti-malware scan.
If you have any reasons to believe that your device is being monitored, you may have to unroot it.
Checking for root or jailbreak
Previously we mentioned that device tapping requires the physical presence of the eavesdropper. Only this way he will be able to intervene on the device.
However, this is a rare case, and specialized knowledge with the right tools are required.
In this case, tapping is much easier to perform with the use of a one-click root application. It is even easier if the device is using an older operating system.
From then on, since your device is rooted without you knowing, it can become an easy target for monitoring. If you that find that this is the case with you, what has to be done immediately is unroot the Android device.
The same can happen to an iOS device, where the eavesdropper had the opportunity to jailbreak it. In this case as well you have to remove the jailbreak by upgrading the operating system.
Encrypting the device
If you own an Android device, then it is a good idea to use the built-in data encryption features.
This way you can drastically reduce the malware attacks aimed at collecting valuable data.
If your device does not have built-in encryption features, it is important not to store sensitive data in it, such as accounts and credit card information.
Factory reset
Experts on mobile safety claim that if the device becomes infected with malicious applications designed to monitor (and not only), it is not clear whether uninstalling them will remove the threat.
The only safe way to permanently get rid of it is to create security backups of all data, and then proceed into restoring the device to factory settings.
However, performing this action in a rooted/jailbroken device may not be effective. In rooted devices, such threats survive even after a factory reset. In this case, a direct unroot/unjailbreak is deemed necessary.
Request assistance from your carrier and authorities
If you have serious reasons to believe that your phone is being monitored, you have every right to ask your carrier to review your complaint, since it certainly has the necessary technical equipment to do so.
However, in most cases it requires permission from the authorities in order to carry out this operation. Once/if approved, the carrier will be able to detect any illegal interceptions.
Is it possible that your phone is being monitored?
Most of you have no particular reasons to believe that your phone is actually being actively monitored. Undoubtedly, it will be a big shock if you discover something that implies the opposite, though.
But if you do come across any of the signs which point towards that direction, it is a good idea to take immediate precautions and prevent the invasion of your privacy, even if there is no concrete proof of that.
If you have any questions, thoughts or suggestions on the topic, please don’t hesitate to share them with us by posting in the comments section below.



