First Attacks Using Bash 'Shellshock' Bug Reported. Here Is How To Check If You Are Vulnerable
As we previously reported, Bash software bug dubbed 'Shellshock' is rated 10 out of 10 for severity, and a 2-4 in complexity, which means it doesn't take a cyberpunk to exploit the vulnerability. In fact, ever since the news broke, hacker community became vibrant discussing worms and other techniques that could be used to exploit the shellshock.
Pair that with the fact that it's not easy to get everyone to update, and get a pretty intense situation. During the past few days, reports of the ongoing attacks trying to exploit Shellshock started surfacing, while some of them were reports of successful hacks. At the same time, security experts release more warning notes about Shellshock being used as an Internet worm to exploit public web servers.
Partially Patched
The initial patch released a couple of days ago left Bash vulnerable to exploits, according to US CERT National Vulnerability Database. In addition, there is a second vulnerability in Bash that allows hackers to overwrite files on a hacked system, and the fix that addresses this vulnerability is yet to be issued.
This Thing Is Wormable
Robert Graham from Errata Security said in his blog that someone is already running a wide-scale Internet scan for vulnerable servers. Graham himself ran a brief scan and located over 3000 vulnerable servers 'just on port 80' - the IP port used by HTTP requests, but his scan broke due to the overwhelming number of vulnerable servers.
"It's things like CGI scripts that are vulnerable, deep within a website (like CPanel's /cgi-sys/defaultwebpage.cgi)," Graham wrote. "This thing is clearly wormable and can easily worm past firewalls and infect lots of systems. One key question is whether Mac OS X and iPhone DHCP service is vulnerable—once the worm gets behind a firewall and runs a hostile DHCP server, that would be 'game over' for large networks."
Check Your System
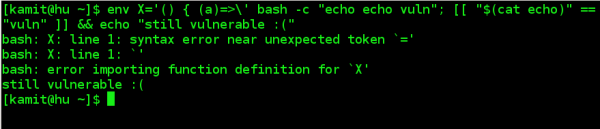
Tavis Ormandy, a Ggoogle security researcher, published in his personal Twitter stream a test he came up with that may help you check whether your copy of Bash is still vulnerable: env X='() { (a)=>\' sh -c "echo date"; cat echo.
If your copy of Bash is vulnerable, indeed, the directory in which you ran the code should display a file named echo. You can delete it while you wait for the next patch:
Reports of Ongoing Attacks
ArsTechnica reports a number of security companies are reporting ongoing Shallshock-based attacks that started 4.5 hours after the bug was publically announced, and the expert expect the attacks numbers grow. “Everybody is scrambling to patch all of their internet-facing Linux machines. That is what we did at Veracode today,” he said. “It could take a long time to get that done for very large organisations with complex networks," said Chris Wysopal, chief technology officer with the security software company Veracode.
AV company Kaspersky already reported the vulnerability "has been used for malicious intentions," including infecting web servers."The key thing to understand is that the vulnerability is not bound to a specific service, for example Apache or nginx. Rather, the vulnerability lies in the bash shell interpreter and allows an attacker to append system level commands to the bash environment variables," states Kaspersky note.
The Fun Has Only Just Begun
At the same time, security researchers at malwaremustdie.org analyzed some attacks and dissected another malware exploiting Bash bug that suggests the attackers are more interested in spying on targets, rather than crippling their systems. As folks at malwaremustdie.org note, 'the fun has only just begun.'
Final Question
My question is rhetoric – can we think of a way to discover bugs, patch them and release patches without letting the world know how to exploit them before we’ve patched, eh?
Sources: LinuxBSDos, ArsTechnica, Zdnet, The Guardian, malwaremustdie.org.