Vulnerability Found & Fixed in Popular Ad Service MadAdsMedia
MadAdsMedia Banner
Cybercriminals exploited vulnerabilities in MadAdsMedia, a web advertising network based on the US, in order to redirect visitors who used this ad platform and force them to download and install Adobe Flash exploits, delivered by the Nuclear Exploit Kit. For those who are not aware of exploit kits, in simple words they are scripts (programs) that take advantage of vulnerabilities found in other applications in order to perform malicious actions.
Attack Details
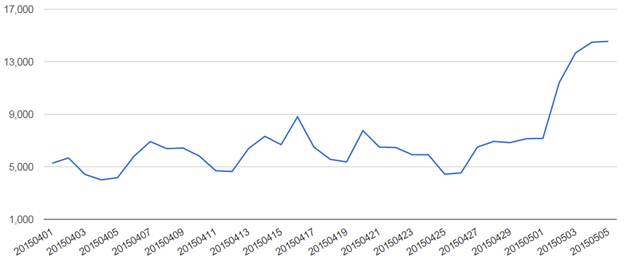
The attack was first seen in April, with more and more users becoming victims every day, reaching 12,500 users on May 2 and a rough estimation of 200.000 – 250.000 in total. Interestingly enough, many of the affected sites had content related to Anime and Manga.
Victims of the attack [Source: Trend Micro Blog]
At first, this anomaly was accredited to malvertising (i.e. “malware advertising”, the act of spreading malware through advertising), but after some more thorough analysis of the case by Trend Micro, it was discovered that it didn’t have specific properties of a typical malvertising scenario.
The Adobe Flash exploit that the cybercriminals took advantage of is CVE-2015-0359, a vulnerability that was patched very recently- in April, which increases the chances of affecting someone, since a lot of users seem to postpone updating their applications.
How It Worked
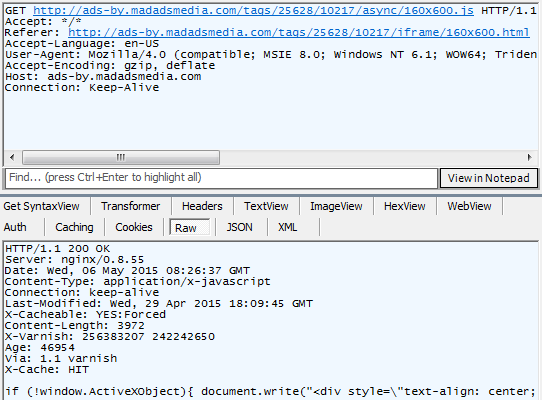
The issue was found in the JavaScript library located in one of MadAdsMedia’s servers, which, under normal circumstances, assigns what kind of advertisement would be displayed in the site, as it’s shown below:
How the JavaScript library should normally work [Source: Trend Micro Blog]
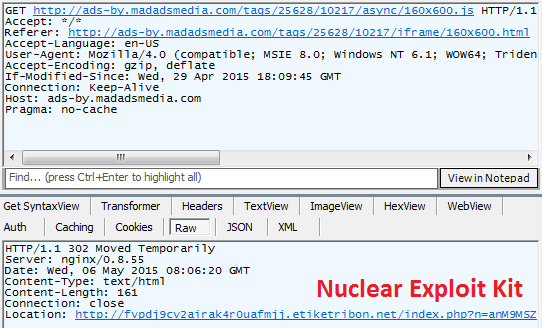
Thus, the attackers probably changed the library in order to make it redirect visitors to the Nuclear Exploit Kit server instead:
How the JavaScript library worked after the attack [Source: Trend Micro Blog]
Patch
As of now (May 8) the affected URL in MadAdsMedia is now fixed. A representative from the popular advertising service stated:
We launched an investigation shortly after noticing suspicious activity in our network. Soon after, we were contacted by Trend Micro; the details from their research played a crucial role in our efforts to eliminate this threat. We provided Trend Micro’s information to our hosting company, GigeNET.com, and they swiftly took action. Within hours, GigeNET identified the breach and simultaneously secured the network. We thank both Trend Micro and GigeNET for their efforts in protecting our users.
It is however, always advised to keep plugins, extensions and software up to date, in order to prevent attacks similar to this one in the future.
[Source: Trend Micro Blog]