Tails OS: Zero-Day Vulnerabilities Allegedly Found. No Proof Provided
There has been a lot of controversy regarding the anonymous browser Tor and the privacy and security focused operating system for the paranoid, Tails. Even though Tails has been around for several years now, it went out of beta only a couple of days ago. Now, Internet is being bombarded with worrying reports - Tor was built by CIA or NSA contractors, Edward Snowden ran several Tor exit nodes as a part of his job at the NSA, and now this - Tails operating system allegedly entails zero-day vulnerabilities.
Ed Snowden’s Privacy Tools
Edward Snowden basically endorsed both Tor and Tails OS as a secure means of going online and remaining anonymous. On more than one occasion, he gave online interviews with Tails or Tor launched on his laptop in the background.
Tails offers a complete suite of applications made to maintain users' identities and online activity anonymous. Besides, it is flashed as a standalone OS from a flash drive or CD, and does not store any information about user's activity. So, once the USB drive or CD is removed, user's computer has no memory or any leftover traces of that Tails activity.
Both Tails and Tor have been making surveillance agencies and the Police of countries worldwide mad enough to ban their usage in some countries. However, the idyllic image of a digital privacy fortress Tails OS might have been ruined by a publication from Exodus Intelligence, a Texas-based security firm.
Let us try and see if there is enough reason to stop using these privacy products.
Zero-Day Vulnerabilities in Tails – Truth or Lies?
The Hacker News reports that, according to Exodus, the above-mentioned vulnerabilities may put an end to Tails users' privacy and security and allow the hacker or the state spy agency unmask the user's location and identity. It does sound like a serious allegation, which immediately outraged the folks at Tails for a good reason - the entity releasing the claim has not provided Tails developers with proof of their findings.
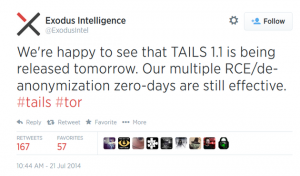 Last Monday, the Exodus Intelligence firm tweeted about multiple zero-day vulnerabilities found in Tails, which allow an attacker de-anonymize a user and run a remote code execution. Exodus Intelligence did not release more details about it, though, stating they did not wish to make the sensitive information public until Tails release an update.
Last Monday, the Exodus Intelligence firm tweeted about multiple zero-day vulnerabilities found in Tails, which allow an attacker de-anonymize a user and run a remote code execution. Exodus Intelligence did not release more details about it, though, stating they did not wish to make the sensitive information public until Tails release an update.
The Bad News Is Published on the Same Day Tails 1.1 Gets Released
Bad news spread like fire in a dry forest, and without waiting for any proof, major tech outlets started publishing reports about Tails having a major security and privacy vulnerability and the operating system's architecture serious weaknesses, and it was high time for the paranoid to take their anti-panic meds and jump the Tails train.
Now, Tails launched its 1.1 version, and Exodus specified that the release contained no patches for the allegedly found vulnerabilities. According to the Hacker News, Exodus Intel sell their findings, mostly vulnerabilities in tech products, to their major clients - DARPA and US state agencies. Allegedly, this time Exodus chose not to sell a backdoor to one of the most coveted privacy suites of today to its clients.
No Place for Ethics in Modern Wars
As a rule, whenever a security firm or an individual researcher discovers a security flaw, the ethics command the finder should contact the manufacturer and wait for the reply, or a patch. If there is no response or a patch for a reasonable time, it is fair enough for the security firm or the researcher to bring the issue to the public attention. Exodus, however, chose to do it the dirty way this time.
Tails developers claim they have not received any details from Exodus until now. In fact, Exodus did not contact Tails developers until after they published that tweet and the news went viral:
"We were not contacted by Exodus Intel prior to their tweet. In fact, a more irritated version of this text was ready when we finally received an email from them. They informed us that they would provide us with a report within a week."
Those using Tails know the community is in constant process of discovering and fixing vulnerabilities, even though there are individuals looking to derive profit from their findings. That is human nature, and the Tails community's strength is in fast response to found threats.
Food for Thought
Until we hear more details on the zero-day vulnerabilities from either Exodus or Tails developers, there is only so much users can do - hold their breath. No code is immaculate, and there is nothing a human genius can't do, so it would not come as a surprise that these vulnerabilities in Tails exist, indeed. However, there are two nagging points here:
- How do we know Exodus really didn't sell their findings to the government, or any private party for that matter?
- Why Exodus chose to first go public with that information instead of contacting Tails developers and let them patch the holes?
The answer is somewhere where the money is, but we have insufficient information to ponder on the underground currents influencing this issue. What we do know is there is a serious media campaign to discredit popular privacy and security tools - Tor, Tails and TrueCrypt. In other words, if you can't break into a security product, force users to drop it. Information war is in its hot phase, and it is important general public can assess the information critically, without swallowing the hand-fed un-truths. Stay tuned to Download3k for more updates on the matter.
Related articles:
